Microsoft Secure Score
Steps to Assess Security Posture
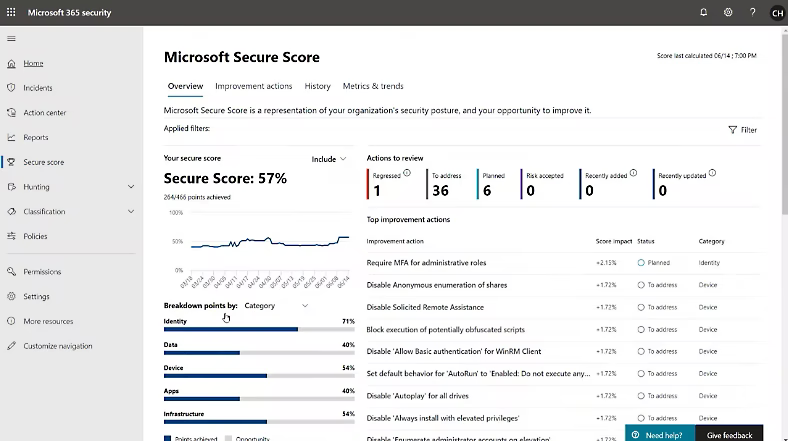
Assessing the state of your security posture across various domains like identity, devices, information, apps, and infrastructure is a critical step in understanding how well your organization is protected against potential threats.
Here’s a guide on how to go about it:
Identity Management
- Evaluate your identity and access management policies.
- Assess the strength of authentication and authorisation mechanisms.
- Review user roles and permissions.
Device Security
- Inventory all devices connected to your network.
- Assess the security configurations, patch levels, and any existing vulnerabilities.
Information Security
- Identify where sensitive data is stored and how it is protected.
- Evaluate data encryption and data loss prevention mechanisms.
Application Security
- Review all internal and external applications used by your organisation.
- Assess them for vulnerabilities and ensure they are updated and patched regularly.
Infrastructure Security
- Evaluate the security of your network architecture.
- Assess firewalls, intrusion detection systems, and other security appliances.
Benchmarking Over Time
- Initial Assessment: Conduct an initial assessment to establish a baseline.
- Regular Audits: Perform regular security audits to assess any changes or improvements.
- Trend Analysis: Use the data collected over time to identify trends, improvements, or deteriorations in your security posture.
Comparative Analysis
- Industry Benchmarks: Compare your security measures against industry standards or benchmarks to see how you stack up.
- Peer Comparison: If possible, compare your security posture with that of similar organisations. This can often be done through industry reports or anonymised data sets.

Identify areas to improve and create a plan
Evaluating recommendations for improving your security posture involves a multi-step process that includes understanding the potential vectors of attack, prioritizing them, and then planning for mitigation.
Here’s a guide on how to go about it: Steps for Using Historical Reports
Understand Embedded Guidance
- Carefully review the embedded guidance that comes with each security recommendation. This could be in the form of documentation, expert advice, or automated suggestions from security tools.
Identify Vectors of Attack
- Use the guidance to identify the various vectors of attack that each recommendation is designed to address. These could range from phishing attacks to unauthorized data access.
Assess Severity and Impact
- Evaluate the potential impact of each vector of attack on your organization. Consider factors like data sensitivity, compliance requirements, and potential financial loss.
Prioritise
- Based on the severity and impact, prioritize the vectors of attack that need immediate attention.
Infrastructure Security
- Evaluate the security of your network architecture.
- Assess firewalls, intrusion detection systems, and other security appliances.
Creating a Posture Improvement Plan
List Improvement Actions
- For each prioritized vector of attack, list down the actions that can mitigate the risk. This could include implementing new security measures, updating existing policies, or employee training.
Assign Responsibility
- Clearly assign who is responsible for each action. This could be an individual, a team, or a department.
Set Deadlines
- Establish realistic but firm deadlines for completing each action.
Resource Allocation
- Ensure that you allocate the necessary resources, be it time, personnel, or financial investment, to carry out each action.
Monitoring and Review
- Set up a mechanism to regularly monitor the progress of each action. This could be through regular meetings, automated tracking, or periodic audits.
Update Plan
- As actions are completed or as new threats emerge, update the posture improvement plan accordingly.
Comparative Analysis
- Industry Benchmarks: Compare your security measures against industry standards or benchmarks to see how you stack up.
- Peer Comparison: If possible, compare your security posture with that of similar organisations. This can often be done through industry reports or anonymised data sets.

Steps to Determine Potential User Impact
Evaluating recommendations for improving your security posture involves a multi-step process that includes understanding the potential vectors of attack, prioritizing them, and then planning for mitigation.
Here’s a guide on how to go about it:
User Experience
- Evaluate how each recommendation will affect the user experience. Will it make systems more cumbersome to use? Will users need to adopt new habits?
Training Requirements
- Assess whether users will require training to adapt to the new changes. This could range from simple email guidelines to formal training sessions.
Access and Permissions
- Consider how changes in access controls or permissions might affect users’ ability to perform their tasks.
Downtime
- Will the implementation of the recommendation require system downtime that affects users?
Data Migration and Loss
- Assess if there’s a risk of data loss during the implementation, and how that would impact users.
Communication
- Plan how to communicate these changes to the users, including why the changes are necessary and how users will benefit in terms of security.
Procedures to Implement Each Recommendation
Feasibility Study
- Conduct a feasibility study to understand the technical and financial implications of implementing each recommendation.
Risk Assessment
- Perform a risk assessment to understand the security vulnerabilities that each recommendation aims to address
Pilot Testing
- Ensure that you allocate the necessary resources, be it time, personnel, or financial investment, to carry out each action.
Monitoring and Review
- If possible, conduct pilot tests to evaluate the effectiveness and potential impact of the recommendation.
Resource Allocation
- Allocate necessary resources, including personnel, time, and budget, for the implementation.
Implementation Plan
- Develop a detailed implementation plan, including steps, timelines, and responsible parties.
Backup and Rollback Plan
- Always have a backup and rollback plan in case the implementation introduces new issues or fails to address the existing ones.
Documentation
- Document the procedures, changes made, and any configurations so that they can be reviewed and audited later.
Monitoring and Review
- After implementation, monitor the systems for any issues and evaluate the effectiveness of the recommendation.
Feedback Loop
- Establish a feedback mechanism for users to report any issues or suggestions related to the new changes.

Steps for Using Historical Reports
Using historical reports to track and maintain progress is a powerful way to keep your security posture in check, identify any backslides, and effectively communicate the state of affairs to leadership teams.
Identify Key Metrics
- Decide on the key performance indicators (KPIs) that will best represent the state of your security posture. This could include metrics like the number of security incidents, time to detect/respond to incidents, compliance levels, etc.
Data Collection
- Ensure that you have mechanisms in place to collect this data consistently over time. This could be automated through various security tools or manually compiled, depending on your setup.
Baseline Assessment
- Use initial reports to establish a baseline for each metric. This will serve as a point of reference for all future assessments.
Regular Reporting
- Generate reports at regular intervals (monthly, quarterly, etc.) to track progress or regressions. Use the same KPIs for consistency.
Trend Analysis
- Analyze the reports to identify trends. Are incidents decreasing over time? Is compliance improving? Are response times getting faster?
Regression Identification
- Use the historical data to identify any regressions or areas where performance has declined. Investigate the causes and take corrective action.
Reporting to Leadership Teams
Executive Summary
- Create an executive summary that provides a high-level overview of the state of security, focusing on key metrics and any significant changes since the last report.
Visual Aids
- Use charts, graphs, and other visual aids to make the data easily digestible. This can help in clearly demonstrating progress or highlighting areas of concern.
Actionable Insights
- Don’t just present data; provide insights and recommendations. If there’s been progress, explain what actions have contributed to this. If there are regressions, outline the steps being taken to address them.
Monitoring and Review
- If possible, conduct pilot tests to evaluate the effectiveness and potential impact of the recommendation.
Measurable Data
- Always back your statements with measurable data. This adds credibility to your reports and helps leadership understand the ROI on security investments.
Future Plans
- Outline any upcoming initiatives or changes that will further improve security. Provide timelines and expected outcomes to keep the leadership team in the loop.
By systematically assessing each of these areas, you can gain a comprehensive understanding of your organisation’s security posture. This not only helps in identifying vulnerabilities but also in prioritising them, so you can allocate resources more effectively to improve your overall security.
Get the best cyberinsurance
Safeguard your organisation from cyber threats by maintaining a robust security posture and investing in cyber insurance. Select insurance providers are now utilising Microsoft Secure Score to offer posture-dependent pricing tailored for small and medium-sized enterprises.
Good articles to read about cyberinsurance.

